Hi !
Disclaimer
Any actions and or activities related to the material contained within this blog is solely your responsibility.The misuse of the information in this website can result in criminal charges brought against the persons in question. The authors will not be held responsible in the event any criminal charges be brought against any individuals misusing the information in this website to break the law.
This script is published for educational use only. I am no way responsible for any misuse of the information.
This article is related to Computer Security and I am not promote hacking / cracking / software piracy.
This article is not a GUIDE of Hacking. It is only provide information about the legal ways of retrieving the passwords. You shall not misuse the information to gain unauthorised access. However you may try out these hacks on your own computer at your own risk. Performing hack attempts (without permission) on computers that you do not own is illegal.
This article explains how to use my PowerShell tool to reveal the passwords used by users of the computers running under Windows 2003, 2008R2, 2012, 2012r2, Windows XP, 7 (32 and 64 bits) 8, and 8.1Steps below are :1) Get the tool2) Extract the files in the ZIP3) Launch PowerShell with Administrator Rights4) Prepare your environment5) Open the tool into PowerShell6) Launch the tool7) Get Windows 7/Windows server 2008 password
1) Get the toolThe first step is to download the tool. You can got it at this Github address which is the official repository : https://github.com/giMini/RWMCSimply click on the download ZIP button at the bottom right of the screen :
2) Extract the files in the ZIP
Right click on RWMC-master.zip you just download (we assumed you download it into d:\donwload) and then on Extract All...
Clic on Extract button
You'll get a folder RWMC-master with the tool.
The files which are in the folder :
3) Launch PowerShell with Administrator Rights
Choose the good version :
- Windows 7 SP1
- x64: Windows6.1-KB2819745-x64-MultiPkg.msu
- x86: Windows6.1-KB2819745-x86.msu
- Windows Server 2008 R2 SP1
- x64: Windows6.1-KB2819745-x64-MultiPkg.msu
- Windows Server 2012 / Windows 8
- x64: Windows8-RT-KB2799888-x64.msu
Once your computer is up-to-date, go to C:\Windows\System32\WindowsPowerShell\v1.0 and then right click on powershell_ise.exe
PowerShell Starting...
And your PowerShell opens !
4) Prepare your environment
Enter this command : "Set-ExecutionPolicy Unrestricted -force"
and press Enter
5) Open the tool in PowerShell
Browse to the place where you extract the tool you download in step 1. In this example, it is underd:\download\RWMC-master\RWMC-master\Reveal-MemoryCredentials, click on Reveal-MemoryCredentials.ps1 and then on Open.
If all went well, you should get this result (the script is opened in PowerShell) :
6) Launch the tool
Great ! Now we can launch the script to reveal all the Windows password of the users who have logged on the machine (and the machine has not rebooted).
Click on the green arrow (or on "F5" on your keyboard)
You'll get two warnings, click Run Once each time :
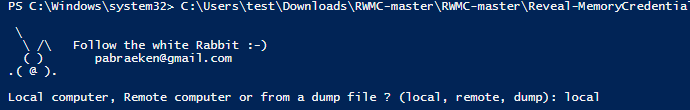
If you see the white Rabbit, you passed the previous steps :-)
7) Get Windows passwords
a) At the prompt, enter the option "local" (to get the passwords on this computer)
...and get the passwords !
Finally, a window opens with all the passwords found on the machine!
b) Remotely
c) From a dump
- 1 = Windows 7 - 64 bits / 2008r2
- 132 = Windows 7 - 32 bits
- 2 = Windows 8/2012
- 2r2 = Windows 10/2012r2
- 8.1 = Windows 8.1
- 3 = Windows XP/2003
Enjoy !